In today’s fast-paced digital landscape, enterprises are rapidly adopting cloud-native architectures to accelerate innovation and achieve greater agility. However, this shift brings with it a complex array of security challenges. Traditional security models, designed for on-premise infrastructure, often fall short in dynamic cloud-native environments. The key to thriving in this new paradigm lies not just in adopting new technologies, but in fundamentally redefining how security is integrated and managed across the entire enterprise. This evolution is driven by a critical need for upskilling teams, fostering cross-functional collaboration, and implementing scenario-based learning.
The Paradigm Shift: Security as Code and Shared Responsibility
Cloud-native security is a departure from the perimeter-focused security of yesteryear. It embraces principles like “security as code,” where security controls are automated and integrated into every stage of the development lifecycle, from initial design to deployment and operations. This approach leverages tools and practices such as Infrastructure as Code (IaC), policy as code, and automated compliance checks.
Furthermore, the shared responsibility model inherent in cloud computing means that while cloud providers secure the underlying infrastructure, the enterprise is responsible for securing everything in the cloud—from applications and data to network configurations and access management. This necessitates a proactive and integrated security posture rather than a reactive one.
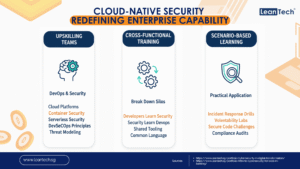
Upskilling DevOps and Security Teams: Bridging the Knowledge Gap
The convergence of development, operations, and security within cloud-native environments demands a new breed of professional. DevOps engineers need to understand security implications and best practices, while security professionals must gain proficiency in cloud platforms, automation tools, and the intricacies of CI/CD pipelines.
Key areas for upskilling include:
-
Cloud Platform Expertise: Deep understanding of specific cloud provider services (e.g., AWS, Azure, GCP), their security features, and configuration best practices.
-
Container Security: Knowledge of securing container images, orchestrators like Kubernetes, and runtime protection.
-
Serverless Security: Understanding the unique security considerations for serverless functions and APIs.
-
DevSecOps Principles: Integrating security tooling and processes into the DevOps pipeline, enabling automated security checks and continuous feedback.
-
Threat Modeling: The ability to identify potential threats and vulnerabilities early in the development process.
Cross-Functional Training Programs: Breaking Down Silos
Effective cloud-native security cannot exist in departmental silos. It requires seamless collaboration between development, operations, and security teams. Cross-functional training programs are essential to foster a shared understanding of security objectives and responsibilities.
These programs should aim to:
-
Educate Developers on Security: Equip developers with the knowledge to write secure code, understand common vulnerabilities, and utilize security tools within their IDEs.
-
Train Security on DevOps: Introduce security teams to agile methodologies, CI/CD pipelines, and automation tools, enabling them to embed security early in the development process.
-
Promote Shared Tooling: Encourage the adoption of integrated security tools that can be used by all teams, promoting consistency and efficiency.
-
Establish Common Language: Create a shared vocabulary and understanding of cloud-native security concepts across all functions.
Scenario-Based Learning: Practical Application and Real-World Readiness
Theoretical knowledge is important, but practical experience is paramount. Scenario-based learning allows teams to apply their skills in simulated real-world situations, preparing them for actual security incidents and challenges.
Examples of scenario-based learning include:
-
Incident Response Drills: Simulating a data breach or a denial-of-service attack in a cloud-native environment, requiring teams to detect, respond, and recover.
-
Vulnerability Remediation Labs: Tasking developers and security analysts with identifying and fixing common cloud-native vulnerabilities (e.g., misconfigured S3 buckets, insecure API gateways).
-
Secure Code Challenges: Gamified exercises where developers compete to build secure applications or find vulnerabilities in existing code.
-
Compliance Audits: Simulating an audit process to ensure adherence to regulatory requirements in a cloud-native setup.
By engaging in these hands-on exercises, teams can develop critical thinking skills, improve their collaboration under pressure, and gain confidence in their ability to manage cloud-native security risks.
The Future is Secure and Collaborative
Cloud-native security is not just a technological challenge; it’s an organizational and cultural transformation. By investing in comprehensive upskilling, fostering robust cross-functional training programs, and implementing practical scenario-based learning, enterprises can empower their teams to build, deploy, and operate secure cloud-native applications with confidence. This redefinition of enterprise capability ensures not only enhanced security posture but also accelerated innovation and sustained competitive advantage in the digital era.
Key Points
What are the 4 C’s of cloud-native security?
Cloud, Clusters, Containers, and Code — the layered framework for securing cloud-native systems.
What is cloud-native protection?
It’s a security approach that safeguards applications, data, and infrastructure built using cloud-native architectures.
What are the four types of cloud security?
Data security, network security, application security, and identity & access management (IAM).
How to secure cloud-native applications?
Integrate security into CI/CD pipelines, use IaC scanning, enforce least privilege, and monitor continuously.
Empower your teams to master cloud-native security. Explore our specialized courses and get started today!